What's SMART! And Why You Need To Check?
Our system's hardware is not perfect at all and they may failed any time without any S.M.A.R.T. warnings.
S.M.A.R.T. (Self-Monitoring, Analysis and Reporting Technology; written also as SMART) is a monitoring system for computer hard disk drives to detect and report on various indicators of reliability, in the hope of expecting failures. When a failure is realized by S.M.A.R.T., the user may choose to replace the drive to avoid unexpected outage and data loss. The manufacturer may also use S.M.A.R.T. to discover where faults lie and how prevent them to designing drives in future. So, SMART gives you some advance warnings, if the hard drive is starting to fail.
Windows doesn't equipped an easy-to-use built-in tool, which shows the hard disk's SMART data. So, we should need a third-party tool to view these info; however, it's possible to check SMART status, through your system's Command Prompt.
To make a quick SMART check, few commands have to be typed at Command Prompt window.
Press Windows Key, type Command Prompt and press Enter.
When command prompt windows opens type wmic, press enter; again type diskdrive get status press enter.
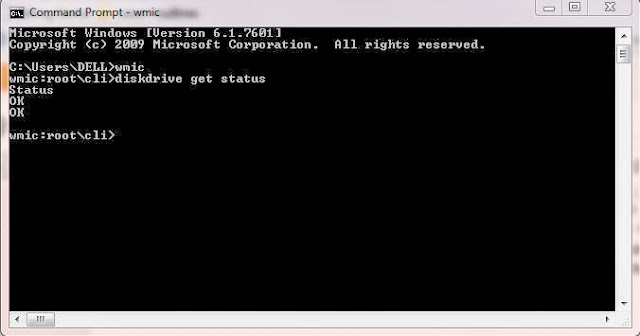 Now the command prompt window reflects SMART status as OK, which means everything is working properly; if the status is showing other than OK, then assume there were some problems or errors in retrieving SMART info.
Now the command prompt window reflects SMART status as OK, which means everything is working properly; if the status is showing other than OK, then assume there were some problems or errors in retrieving SMART info.
Using a third-party tool will also display SMART status of hard drive in Windows.
Crystal Disk Info is a third-party, open source, easy-to-use program, which reveals not only the SMART status of hard drive, but included temperature, and hardware specifications. If there will be a problem or error, you may identified what exactly is wrong with the hard drive. Make sure to un-check the browser's widget, while installing it. If everything works properly, you may see the status as Good.
However, when using either of the above or other reputable programs, if you found an error that doesn't mean the hard drive is going to fail immediately. But you should assume that the drive is in failing process, where a complete failure may occur in few hours, few days, or few months. How long it takes for complete failure, and you shouldn't trust the hard drive with your precious data. Your data on hard drive should be back-up every time on another media, such as an external hard drive or burned discs.
If a hard drive fails in SMART test, then it shouldn't be reliable, even the hard drive doesn't die completely and may corrupt the portions of the data.
However, when using either of the above or other reputable programs, if you found an error that doesn't mean the hard drive is going to fail immediately. But you should assume that the drive is in failing process, where a complete failure may occur in few hours, few days, or few months. How long it takes for complete failure, and you shouldn't trust the hard drive with your precious data. Your data on hard drive should be back-up every time on another media, such as an external hard drive or burned discs.
If a hard drive fails in SMART test, then it shouldn't be reliable, even the hard drive doesn't die completely and may corrupt the portions of the data.